Blockchain Security: How Safe Is Your Data?
Mia Wilson

Photo: Blockchain Security: How Safe Is Your Data?
Blockchain technology has revolutionized various industries by offering a secure and transparent way of storing and sharing data. Its distributed ledger system provides an immutable record of transactions, making it an attractive solution for businesses and individuals seeking enhanced data security. However, as blockchain gains popularity, questions about its security and the safety of data stored on it arise. This article delves into the world of blockchain security, exploring its strengths, potential vulnerabilities, and the measures in place to protect your data.
Understanding Blockchain Security
The Basics of Blockchain
Blockchain is a decentralized digital ledger that records transactions across multiple nodes, making it nearly impossible to alter data without detection. Each block in the chain contains a cryptographic hash of the previous block, a timestamp, and transaction data. This design ensures that once data is recorded, it becomes extremely difficult to modify without leaving a trace.
Security Features of Blockchain
Decentralization
At the heart of blockchain's security is its decentralized nature. Unlike traditional databases, blockchain distributes data across a network of computers (nodes), making it highly resilient to attacks. Hackers would need to compromise a majority of the network's nodes to manipulate data, which is a challenging feat.
Cryptography
Blockchain employs advanced cryptographic techniques to secure data. Each transaction is encrypted, and users are identified through unique digital signatures, ensuring data integrity and user authentication.
Consensus Mechanisms
Consensus mechanisms like Proof of Work (PoW) and Proof of Stake (PoS) validate transactions and add new blocks to the chain. These mechanisms require nodes to solve complex mathematical puzzles, making it computationally expensive for malicious actors to manipulate the system.
Is Blockchain Data Truly Secure?
While blockchain technology boasts impressive security features, it is not entirely immune to threats. Understanding potential vulnerabilities is crucial to comprehending the overall security of the system.
Potential Risks and Vulnerabilities
Smart Contract Exploits
Smart contracts, self-executing contracts with the terms of the agreement directly written into code, can have vulnerabilities. Poorly coded or malicious smart contracts may lead to data breaches or financial losses. The infamous DAO attack in 2016, which resulted in a significant Ethereum fork, is a prime example of a smart contract exploit.
51% Attacks
A 51% attack occurs when a single entity gains control of the majority of the network's mining hash rate. While difficult, this could allow an attacker to manipulate transactions and double-spend coins, potentially compromising data integrity.
Phishing and Social Engineering
Blockchain users are not immune to phishing attacks and social engineering tactics. Malicious actors may trick users into revealing private keys or sensitive information, leading to unauthorized access to data.
Ensuring Data Safety on Blockchain
Despite these potential vulnerabilities, blockchain remains a highly secure technology with robust measures to protect data.
Security Measures in Place
Multi-Signature Authentication
Multi-signature (multisig) authentication requires multiple private keys to authorize a transaction, adding an extra layer of security. This makes it significantly harder for hackers to gain unauthorized access.
Regular Audits and Updates
Regular security audits and software updates are essential to identify and patch vulnerabilities. Blockchain networks undergo rigorous testing to ensure the security of smart contracts and the overall network.
Cold Storage
For long-term storage of sensitive data, cold storage solutions are employed. These are offline wallets or hardware devices that are not connected to the internet, making them immune to online hacking attempts.
Best Practices for Users
To ensure the safety of your data on blockchain, consider the following:
- Private Key Management: Safeguard your private keys and never share them with anyone. Consider using hardware wallets for added security.
- Stay Informed: Keep up-to-date with the latest security practices and potential threats. Regularly review blockchain security resources and news.
- Smart Contract Due Diligence: When interacting with smart contracts, ensure they are from trusted sources and have undergone thorough security audits.
- Use Secure Exchanges: Choose reputable cryptocurrency exchanges that prioritize security and offer two-factor authentication.
Conclusion
Blockchain technology offers a robust and secure way of storing and sharing data, but it is not infallible. By understanding the potential risks and implementing best practices, users can significantly enhance the security of their data on the blockchain. The combination of blockchain's inherent security features and user vigilance creates a powerful defense against malicious activities.
As blockchain continues to evolve, ongoing research and development will further strengthen its security, making it an increasingly reliable solution for data protection in various sectors. While challenges remain, the benefits of blockchain's security, transparency, and immutability make it a compelling choice for businesses and individuals seeking data safety in the digital age.
For You
View AllPlan your solo adventure without overspending. These 7 budget travel hacks are perfect for independent travelers!
Mia Wilson
Save money while traveling with these 10 genius budget travel hacks. Explore the world without emptying your wallet!
Mia Wilson
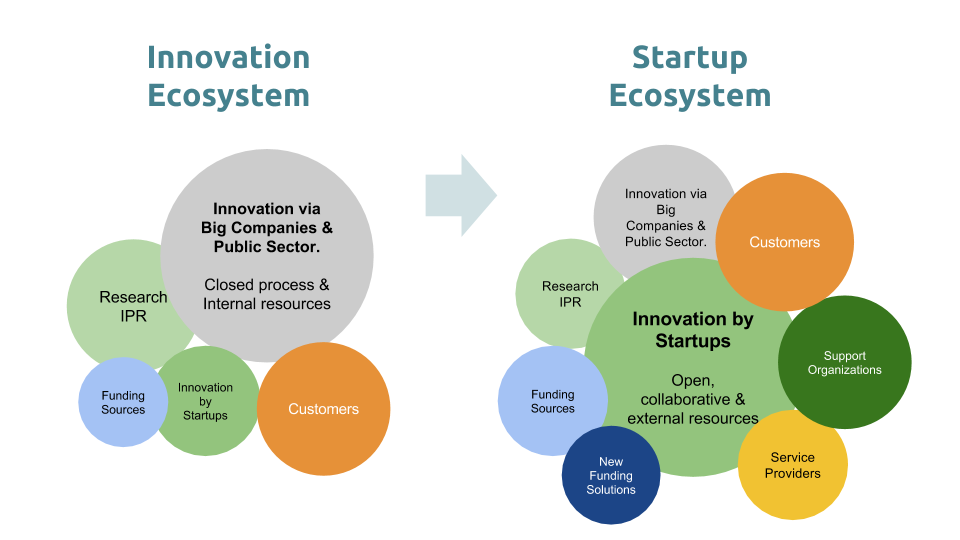
Learn about the startup ecosystem, key players, and what drives innovation. Click to explore this vibrant community!
Mia Wilson
Understand continuing education, its benefits, and how it boosts career growth and lifelong learning. Learn more!
Mia Wilson
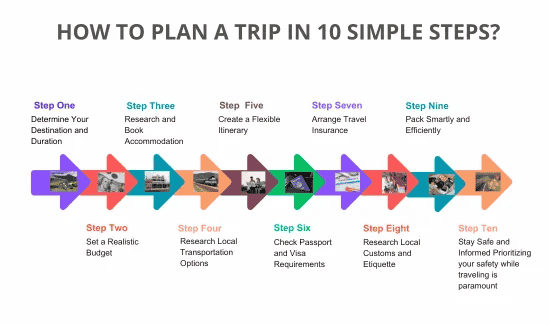
Discover 10 ideal travel itineraries designed for beginners. Simplify your trips with these easy-to-follow plans for stress-free travel!
Mia Wilson
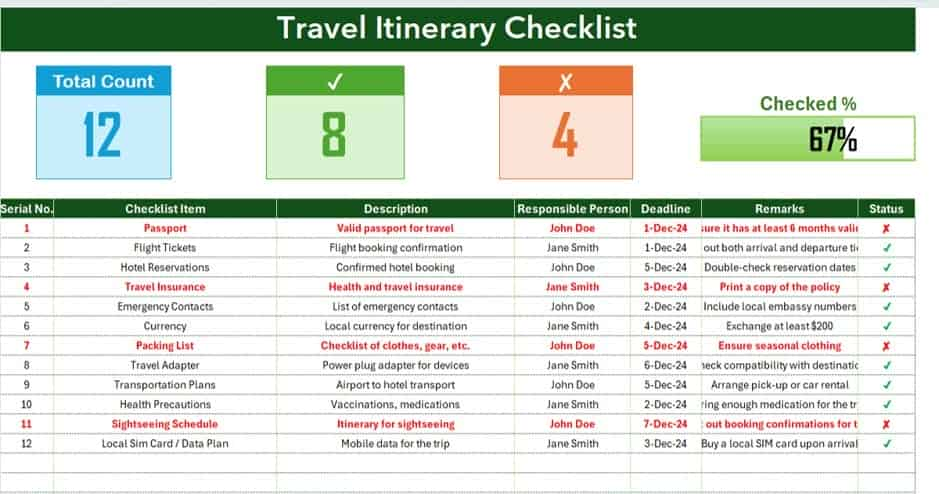
Never miss a detail with this travel itinerary checklist. Ensure your trips are smooth, organized, and unforgettable with these essential tips!
Mia Wilson
Education
View All
April 22, 2025
What Is Early Childhood Education?
Explore early childhood education, its benefits, and how it shapes a child’s future. Start building strong foundations!

April 24, 2025
What Is Distance Education? Explained!
Discover how distance education works, its benefits, and how it’s transforming learning. Start your journey today!
May 6, 2025
What Can You Do With a Master’s in Education?
Explore the career opportunities and advancements possible with a master’s in education. Take the next step today!